Here’s how to set up user and data security policies that reduce risks, safeguard information, and ensure the right people have the right level of access.

Most organizations have some rules about where things should be stored and who can see what. Fewer have rules they reliably enforce. That gap is where risk lives—siloed unsecure systems, over-shared folders, orphaned accounts, no version control, and documents that linger long past their retention window.
This guide walks you through a practical approach to setting security and user access policies you can operationalize in any capable document management system (DMS). We’ll help you assess your current risks, define clear guardrails, and turn policies into permissions, retention schedules, and audit trails. You’ll also learn how to move from tediously managing information to effectively implementing it when your policies are powered by a DMS like DocuXplorer.
Security and user data policies are the backbone of safe, efficient operations. Done well, they prevent data leaks, unauthorized access, and costly non-compliance—while keeping your team productive. Clear document control policies define who can access which records, under what conditions, and for how long. A DMS then enforces those rules consistently, tracks every change, and speeds up audits with complete event logs.
Think of your policies as the map and your DMS as the GPS, guiding you along the safest, most efficient route and adjusting for errors—so you stay on track without having to second-guess every turn.
Begin with a quick, honest data health check that answers these questions:
Turn your findings into a list of the top risks and gaps—you’ll use this list to prioritize the policies you implement.
A strong data security policy framework should cover:
DocuXplorer supports configuarable lifecycles for different document types.
Track changes and reduce confusion by using DocuXplorer’s built-in versioning. Set version control by default or on a document-by-document basis.
DocuXplorer enables you to keep detailed event logs to support internal reviews and regulatory audits. Track every action taken on a document, when it was taken, and by whom. DocuXplorer also provides a Library Event Log with data on every action taken on every document in the Library for more detailed reporting.
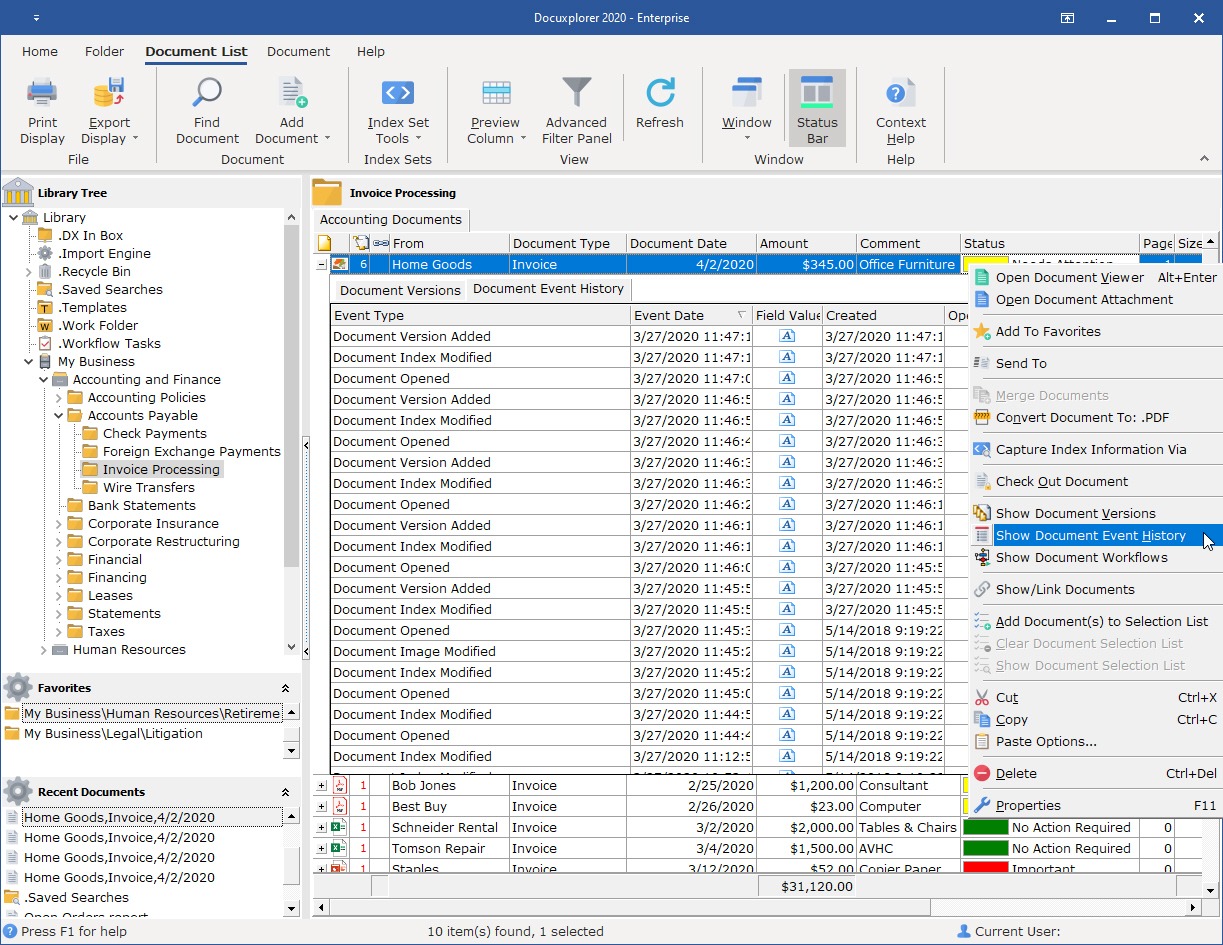
DocuXplorer utilizes 256-bit encryption and supports compliance with GDPR, HIPAA, and other standards.
Design access around roles and the principle of least privilege. Grant the minimum permissions a role needs to perform its duties—no more. Use groups to avoid having to manage users one-by-one (e.g., HR, Finance, Legal). For especially sensitive content like salary data or health info, add a narrower subgroup or per-folder exception.
DocuXplorer tip: Create permission templates per department, then apply them to folders and document classes to keep configurations consistent and auditable.

Document repositories, document types, sensitivity (public, internal, confidential, restricted), and owners.
Identify where sensitive data is mixed with general content and separate it. Move restricted documents like payroll and protected health information (PHI) into clearly segmented locations.
List core roles across the organization, grouped by department and function. These can include:
For each role, define allowed actions (view, add, edit, delete, share) by document class. Assign data owners who can approve access exceptions and retention changes.
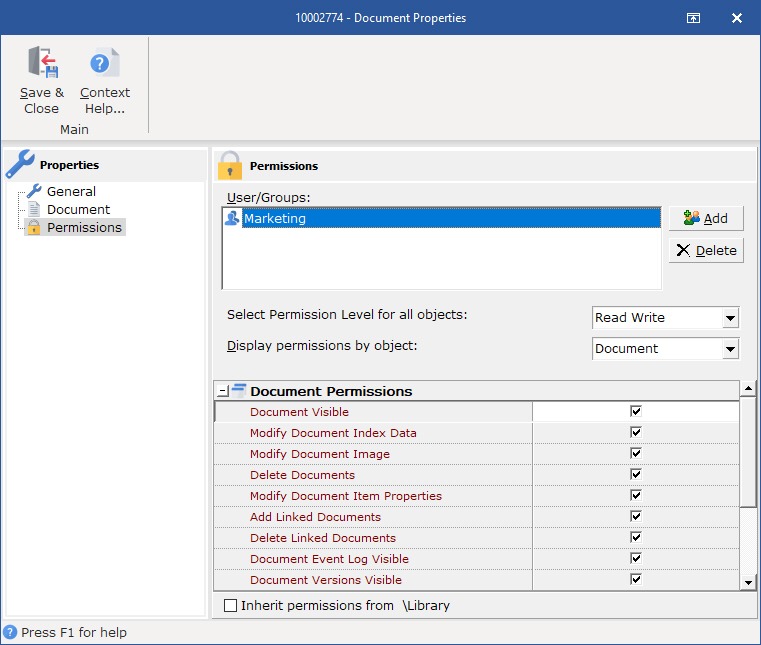
Start with the most strict rules as your default. Add Separation of Duties (SoD) where it reduces fraud or mistakes (for example, an AP clerk cannot both create and approve invoices).
In your DMS, implement read vs. write vs. admin permissions at the folder/document level.
For each document class, define: retention period, authority (law/regulation/contract/business need), final disposition method (secure delete, archive), and hold procedure (who can place or remove holds; how holds override deletion).
Configure these schedules in your DMS so destruction is automated and logged.
Require check-in and check-out (or equivalent) for controlled documents. Write a simple document control policy for change notes (why the edit was made) and approvals for critical documents (e.g., policies, contracts). Ensure the DMS keeps prior versions and timestamps for who did what.
Enable event logging for views, edits, deletes, permission changes, failed logins, and exports. Set threshold alerts for things like mass downloads and permission changes outside business hours. Schedule a monthly audit review for data owners to spot anomalies.
Encrypt your data at rest and in transit. For web-based systems, require MFA (multi-factor authentication) for all users with access to confidential or restricted data, and for any admin role. Where possible, integrate SSO to centralize identity and simplify de-provisioning, and create emergency overrides so that work continues if SSO or permissions are disrupted.
For the desktop version of your DMS, standard access permissions and local encryption are essential. Focus on robust password policies and user account management, while taking full advantage of MFA, SSO, and advanced identity controls if you access the software from the web or use cloud hosting.
Write a brief “How we handle documents” guide. Train new hires on classification, sharing rules, and where to store files (in your DMS, not on desktops). Build offboarding steps: disable accounts, transfer ownership, and review any personal archives or local copies.
Review and refresh your data security policy at least annually. Use DMS reports that show permissions, retention, and potential gaps as your agenda. Also, trigger reviews after organizational changes (restructures, mergers, or new regulations).
When exceptions are granted (temporary access, retention override), record who approved them, the scope, and the expiration date—and set a reminder to revoke. After incidents (like a mis-share), run a brief post-mortem, and update the policy or configuration to prevent repeats.
A DMS should make your policies operational, not aspirational. Evaluate these capabilities:
Security and access policies aren’t about locking work down; they’re about enabling work to happen safely. Start taking control by conducting a data health check, defining basic access rules, setting retention schedules, and letting your DMS enforce the rules you write.
Whether you’re using DocuXplorer or another platform, the goal is the same: fewer surprises, faster audits and reporting, and confident teams who know where to find what they need—and what the rules are.
Some final tips for a successful document control policy:
Knowing your business information’s vulnerabilities is the first step to figuring out what is slowing you down. Then, you can resolve these inefficiencies and get your information back to working for you.